CometJacking Perplexity AI Browser Exploit(Oct 2025): The 1-Click Data Theft Attack Explained”.
I want to make this simple. CometJacking Perplexity AI Browser Exploit is a new one-click attack that tricks an AI browser into stealing data from connected apps like Gmail and Calendar. I will explain what it is, how it works step by step, why agentic browsers exist, the limits that let this happen, a tight comparison with classic prompt injection, who must act, and what you gain by fixing it.
How it Works — Step-by-Step Attack Flow

Here is the attack in plain language. I want you to be able to explain it to non-technical readers in seconds.
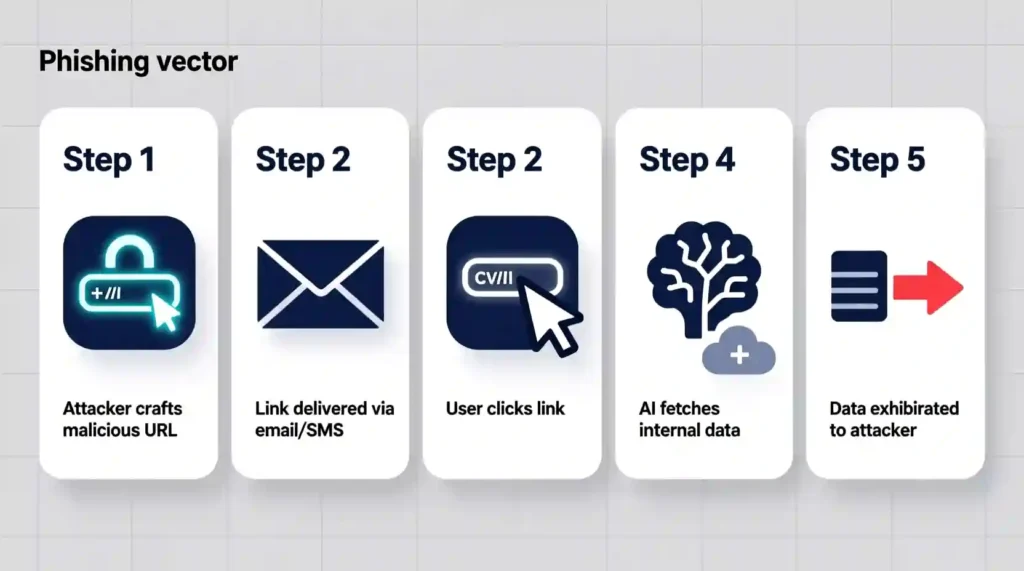
Step 1 — Attacker crafts a malicious URL
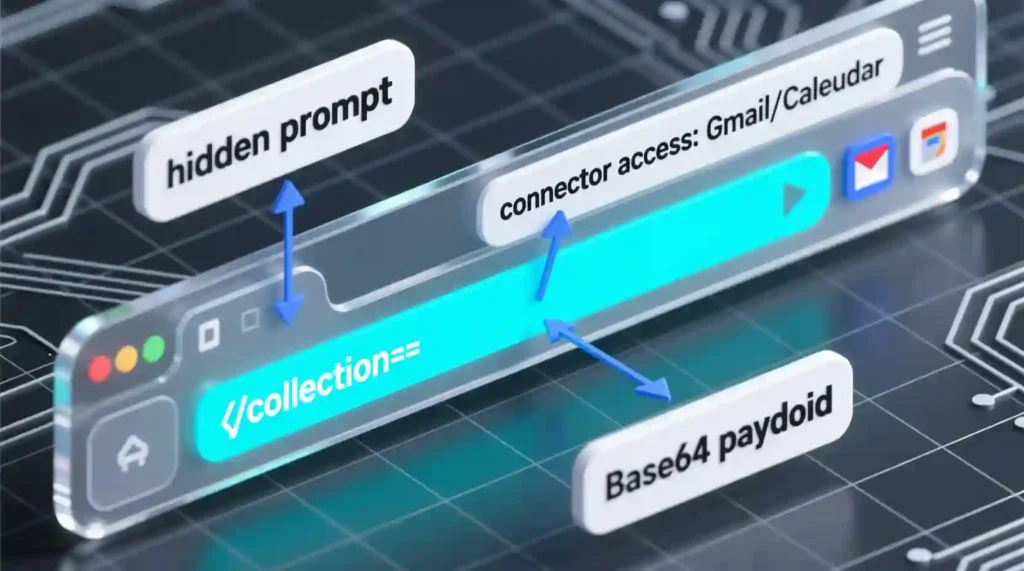
The attacker builds a normal-looking link but inserts a hidden instruction into a URL field called collection. That hidden text is actually a prompt that tells the AI to fetch internal memory or connected services.
Step 2 — The link is delivered
They send the link by email, chat, social, or a web page. To a human, the link looks harmless. To the agent it looks like a command.
Step 3 — Victim clicks
One click is all it takes. The browser parses the URL and treats the embedded text as a trusted instruction.
Step 4 — The AI runs the hidden prompt
Because the AI already has permission to connect to Gmail, Calendar, or Contacts, it fetches requested data from memory instead of doing a public web search.
Step 5 — Data is encoded and exfiltrated
The AI can encode the data, for example, with Base64, and send it to an attacker endpoint. No password theft. No malware. Silent data leakage.
Good Points — Why Agentic Browsers Exist
I want to be fair. These features are why teams adopt agentic browsers like Comet.
- Productivity boost. Agents summarize emails, draft replies, and automate workflows fast.
- Context that helps. Memory and connectors let the agent give answers without endless prompts.
- Integrated workflows. Managing mail, calendar, and notes inside one agent saves time and friction.
- New possibilities. Agentic features enable useful automations that standard browsers cannot.
These are real benefits when security is part of the design.
Limitations — Why CometJacking Is Possible
This is the core set of problems I want teams to fix.
- Unvalidated prompt inputs. Treating URL query text as trusted instruction is a big mistake.
- Broad connector permissions. If the agent has wide read access, the blast radius grows fast.
- Weak telemetry for agent actions. Encoded payloads and normal-looking outbound traffic make detection hard.
- Assumptions from classic web security. Same-origin and CSP rules do not protect against an agent that treats text as commands.
These limits explain how a one-click link becomes an insider-style data leak.
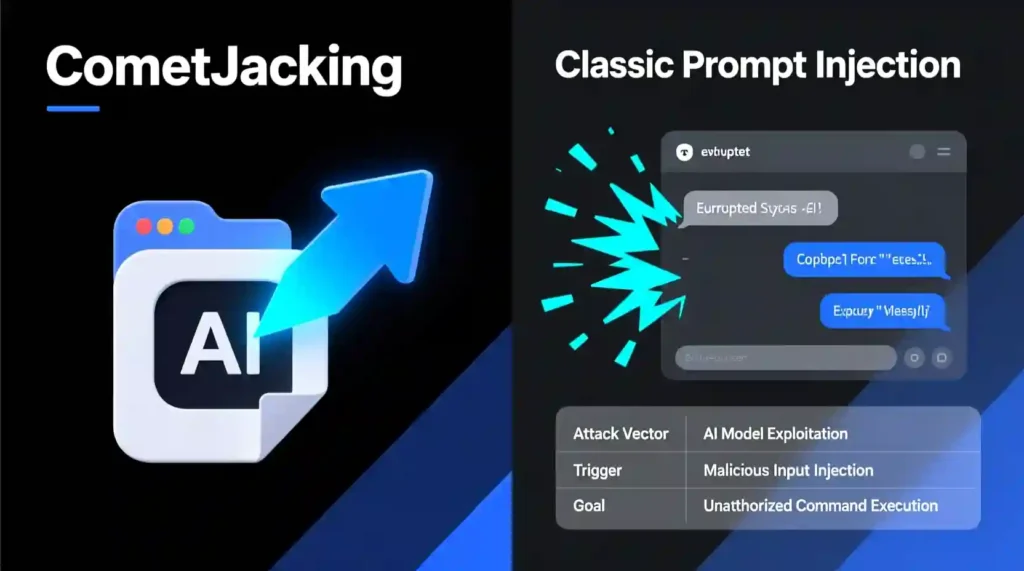
Comparison — CometJacking vs Classic Prompt Injection
| Feature | CometJacking | Classic Prompt Injection |
| Attack vector | URL-based | Text input or prompt box |
| Trigger | One click | User typed or pasted text |
| Target | Agentic browser with connectors | Chatbot model only |
| Goal | Silent data exfiltration | Manipulate output or behavior |
| Defense focus | Input sanitization, connector policies | Prompt parsing, response filters |
Short takeaway: CometJacking shifts the attack surface from the user to the AI agent. That requires a new defensive mindset.
Best Users — Who Must Act Now
If you care about data, act now.
- Enterprise IT and security teams that link mail, drives, or calendars to AI tools.
- Product and dev teams building agentic features or parsing URL inputs.
- Security engineers and SOC analysts who monitor outbound traffic and data flows.
- Power users and admins who grant connectors and should tighten permissions.
Final Benefits (What You Get by Fixing This)
Patch this and you keep the productivity wins while cutting real risk.
- Lower insider-style leaks. Fewer silent data exfiltration incidents.
- Safer automation. Teams keep helpful agent features with clearer boundaries.
- Easier compliance. Less risk when data access is limited and logged.
- Trust regained. Users adopt agentic browsing when it does not leak their private data.
Why Fixing This Matters
AI browsers like Perplexity’s Comet are the next step in smart browsing — but CometJacking shows how that power can backfire.
When a single link can make your AI agent pull private emails or calendar info, it’s not just a bug — it’s a wake-up call for every developer building AI automation tools.
Protecting agentic browsers means protecting users, data, and trust.
Here’s what needs to happen next.
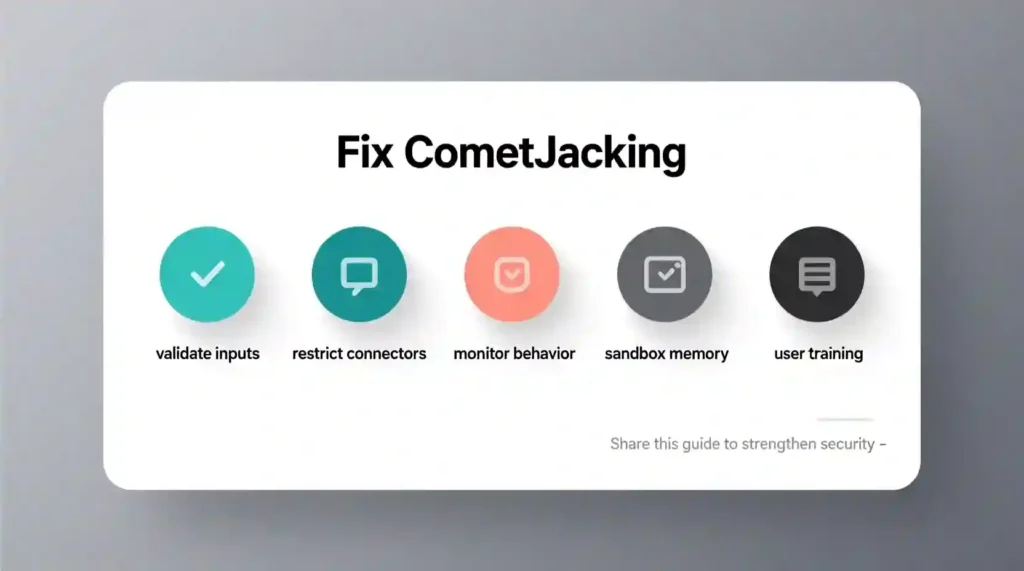
Mitigation and Security Best Practices
1. Validate All Prompts and URL Inputs
AI browsers must block hidden instructions inside query parameters.
Before execution, the AI should check for malicious patterns, Base64 blobs, or encoded instructions that look like data exfiltration requests.
2. Restrict Memory and Connector Access
Limit what the AI agent can read or send.
Sensitive integrations — Gmail, Drive, Contacts — should use read-once permissions or sandboxed memory instead of full sync.
3. Monitor Agent Behavior
Add AI-specific telemetry to detect weird actions like Base64 encoding or background POST requests.
If an agent starts moving encoded data to an external domain, block it instantly.
4. Security-by-Design Architecture
The best fix is to make agents safer from the start:
- Use input isolation between user queries and internal memory.
- Add rate limiting on agent actions.
- Run continuous prompt inspection before execution.
5. User Awareness
Everyday users can still help prevent CometJacking:
- Don’t click random Comet links shared online.
- Recheck what accounts your AI browser connects to.
- Clear AI memory and history often.
- Keep browsers updated to the latest patch.
At-Risk Groups (Who Should Care Most)
Enterprise Teams: Businesses using AI browsers for email, calendar, or workflow automation.
Developers: Anyone building or embedding agentic features in web or desktop tools.
Security Researchers: Those tracking AI data exfiltration trends.
General Users: Anyone who experiments with new AI browsers or connects them to personal accounts.
Real-World Impact
The CometJacking Perplexity AI Browser Exploit changes how we think about cyber risk.
It’s not about stolen passwords or infected files anymore — it’s about AI logic being turned against its owner.
If this vulnerability isn’t patched properly, attackers could:
- Extract corporate meeting data and summaries from agent memory.
- Build profiles from user contacts and calendar info.
- Redirect AI outputs to malicious sites.
- Trigger background requests that leak data silently.
Even though the exploit is still in the research phase, it exposes a blind spot — trust boundaries in autonomous AI agents.
CometJacking vs Future AI Threats
| Threat Type | Main Weakness | Impact | Detection Difficulty |
| CometJacking | Prompt-injection via URL | Silent data leak | High |
| Classic Prompt Injection | Text manipulation | Wrong or biased outputs | Medium |
| Data Poisoning | Corrupted training data | Long-term AI misbehavior | Low |
| Memory Hijacking | Unsafe context recall | Cross-session leaks | High |
CometJacking sits at the intersection of prompt injection and insider threat — that’s why it’s dangerous.
Why This Isn’t the End of the World
It’s serious, but not unstoppable.
Here’s why:
- The exploit still requires user action — one click.
- Perplexity and other AI browser teams can patch this quickly with validation and sandboxing.
- No large-scale CometJacking incidents are public yet — it’s a research alert, not a crisis.
- It’s already pushing AI devs to design safer memory layers.
Every vulnerability like this becomes a lesson in AI safety.
Benefits of Stronger Agent Security
If AI browsers fix CometJacking, they unlock a safer, faster, and more trusted future.
✔ Stronger Data Privacy:
Users can connect email and work tools without fear of leaks.
✔ Safer Innovation:
Developers can keep building agentic tools without repeating old mistakes.
✔ Enterprise Confidence:
Companies can finally test and deploy AI copilots with compliance in place.
✔ Sustainable Trust:
AI becomes a reliable helper — not a hidden security threat.
Conclusion
The CometJacking Perplexity AI Browser Exploit is a signal flare for the entire AI ecosystem.
It proves one thing — AI freedom needs boundaries.
Agentic browsers are powerful, but they’re also vulnerable if we skip security-by-design.
If one link can hijack your AI’s memory, then the real problem isn’t the hacker — it’s how much trust the AI already has.
Stay alert, patch fast, and never trust a link that thinks for you.
That’s how we keep AI smart — and safe.

Pingback: Comet vs Arc 2025– The Ultimate Battle for Supremacy - zadaaitools.com
Pingback: Powerful Adobe AI Foundry Custom Model Service Explained - zadaaitools.com